
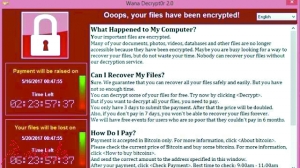

A few days after the ransomware "Want to Cry" raged around the world, the tracing behind the scenes finally got a little clue: Kaspersky Lab in Russia and Symantec in the United States said on the 15th that this ransomware may be related to a hacker organization called lazarus. In this cyber attack, they made malicious ransomware by using the hacking tool "Eternal Blue" leaked from the National Security Agency (NSA) network arsenal.
Reuters once reported that 90% of the expenditure on network projects in the United States was used to develop hacker attack weapons, which could invade the "enemy’s" computer network, monitor people, and paralyze or block infrastructure. Cyber security experts accuse the United States of investing heavily in developing hacking tools instead of self-defense mechanisms, making the global network environment "more insecure".
Compiled by Wen Junhua, all-media reporter of Guangzhou Daily
"The ransomware is not developed by the US National Security Bureau, but by criminal gangs, which may be criminals or foreign governments." Bossert, Assistant to the US President for Homeland Security and Counter-Terrorism, said in response to the "Want to Cry" ransomware incident on 15th, but he evaded the question whether the hacking tools leaked by US intelligence agencies would lead to more cyber attacks in the future.
In fact, the leak of the NSA network arsenal that caused the ransomware rampage was disclosed as early as last August. At that time, a hacker organization named "Shadow Intermediary" claimed to have broken into the "Formula Organization" hacker organization under the NSA and stolen its network arsenal. The "shadow middleman" leaked some of the hacking tools and data through social platforms, and publicly auctioned the complete data package at a high price of 1 million bitcoins (worth about 568 million US dollars), but the hawking did not attract response and widespread attention, and eventually it was auctioned.
Since then, the "shadow middleman" has tried several times to sell the NSA network arsenal without success. Its latest exposure of NSA network weapons was released in mid-April this year. The organization said that NSA had invaded the international banking system to monitor the capital flow between some banks in the Middle East and Latin America. The hacking tool "Eternal Blue" of NSA network arsenal is believed to have been leaked by "shadow middleman".
Although the profit-making purpose of the "shadow middleman" has not been realized, the statement that the hacking tools it stole originated from NSA is considered to be highly reliable. Last year, when the "shadow middleman" released some hacking tools and data, Snowden, the exposer of the "Prism Gate" incident, provided an NSA "malware implantation operation manual" to prove that the cyber weapons peddled by the "shadow middleman" carried NSA’s virtual fingerprints. For example, NSA’s "Malware Implantation Operation Manual" instructs operators to use a special 16-bit string "ace02468bdf13579" when using a malware program SECONDDATE. Among the dozens of hacking tools leaked by "Shadow Broker", the tool SECONDDATE is one of them, and its related code contains a large number of this string.
When it comes to the NSA network arsenal, you can’t avoid the "equation organization". This hacking organization is considered to be a "unwilling to admit" department of NSA, similar to the "fantasy bear" hacking organization in Russia. Before being caught by Kaspersky Lab in 2015, Equation Organization was secretly active for 15 years. According to media reports, because the time and money spent on malware development, mobile technology breakthrough and target blockade are all funded by the state, the project resources are almost unlimited, and Equation Organization has become the "best" hacker organization in the world.
Iran, Russia, Pakistan, Afghanistan, India, Syria, and Mali are among the top 500 infections in 42 countries made by Formula Organization previously announced by Kaspersky Lab. Due to the built-in self-destruction mechanism of malware, the attack of Equation Organization is difficult to be tracked. Therefore, the hacker tools leaked from this arsenal and some previously exposed attack methods can only represent the tip of the iceberg of the NSA network arsenal.
Some NSA cyber weapons
The "Equation Organization" under NSA was discovered and named by Kaspersky Lab. The name comes from their preference for using powerful encryption methods in cyber attacks. In the previous network attacks, they used various attack methods, such as worms, hard disk viruses, spyware, and network-based attacks.
Fanny worm virus
Fanny worm is the most powerful worm, which can invade the network isolated by the gateway. Fanny worm virus uses a unique USB-based control mechanism, which is mainly realized by USB disk infection.
There is a hidden storage area in the U disk to collect basic system information from the isolated network. When the U disk infected with worms is inserted, the collected information can be immediately sent to the attacker in the networked state. If attackers want to run instructions on the network environment isolated by the gateway, they can store the instructions in the hidden space of the U disk through a worm. When the U disk is inserted into the target computer, the worm will automatically recognize and run the instructions.
"Shenzhen" virus
It is reported that "Shenzhen" is the first destructive virus specially written for industrial control system, which contains the vulnerability intrusion technology of Fanny worm virus, and can attack Windows system and Siemens SIMATIC WinCC system by using seven vulnerabilities. It is said that it was jointly developed by the United States and the Israeli government.
The structure of "Shenzhen" virus is extremely complicated and its concealment is super strong. After the computer operator inserts the infected U disk into the USB interface, this virus will gain control of the industrial computer system without any operation.
During the attack on Iran’s nuclear facilities, the virus suddenly changed the engine speed in the centrifuge. This sudden change was enough to destroy the centrifuge’s operation ability and could not be repaired. After the centrifuge was out of control, the virus still sent a report of "working normally" to the control room, so that the centrifuge was destroyed without anyone knowing. spyware
Regin spyware is an advanced stealth malware discovered by Symantec in 2014, which can avoid the detection of conventional anti-virus software. The malware has been accused of being used to monitor the government, companies and individuals since 2008 and is considered to be associated with the NSA.
Symantec pointed out that Regin spy tool uses a number of stealth technologies, which requires a lot of time and resources, indirectly indicating that it is a product developed by a "country". Regin malware allows hackers to launch a series of remote Trojan attacks, including stealing users’ passwords and data, intercepting users’ mouse clicks, capturing screenshots from infected computers, monitoring network traffic, and analyzing emails from Exchange databases. Hard disk virus
A report by Kaspersky Lab has revealed that NSA may have implanted a virus in the hard disk firmware to rewrite the hard disk firmware of the infected computer.
According to the report, because the virus is written into firmware, it can be activated after the hard disk is powered on. This malicious firmware creates a secret information repository, which can effectively prevent military-level disk erasure and reformatting, so that sensitive data stolen from victims can still be used even after reformatting the driver and reinstalling the operating system.
PHP intrusion code
Equation organization has been found to use malicious PHP intrusion code to attack loopholes in Oracle’s Java software framework or IE browser, ranging from scientific and technological product evaluation to various websites of Islamic Jihad forum. This invasion is as precise as surgery, which can ensure that only one specific target is infected. In an invasion case, the PHP script of Equation Organization also paid special attention to avoid infecting the IP addresses of Jordan, Turkey and Egypt.