In 2010, the 90th meeting of the 64th UN General Assembly adopted a formal resolution to designate October 20th, 2010 as "World Statistics Day". This is the first global statistics day in history, and global statisticians have ushered in their own common festival. Five years later, the 69th United Nations General Assembly officially designated October 20th as World Statistics Day, which is celebrated every five years. As a grand event that transcends national boundaries, World Statistics Day highlights the concept of "global statistics are one" and enhances the importance of official statistics and public recognition.
I. Origin of "World Statistics Day"
After the end of World War II, all countries are healing the wounds of war and restoring and developing their economies. In this process, official statistics began to play a role in social and government decision-making, especially in important areas of people’s livelihood such as economy, population and health. With the continuous development and progress of economy and society, the national statistical agency responsible for producing and disseminating official statistical data has become one of the important national institutions in every country, and statistical data has also become an important basis for government decision-making, academic research and public knowledge.
Worldwide, the United Nations established the Statistical Commission in 1947, which is responsible for formulating international statistical standards, methods and guidelines, and promoting the standardization and global comparability of statistics in all countries of the world, the improvement of methods and systems and the improvement of data quality. Nowadays, global statisticians cooperate sincerely, and official statistics have formed a closely linked world family. Every year, heads of statistical agencies of United Nations member countries and international organizations gather in new york to make decisions on various statistical issues at the annual meeting of the United Nations Statistical Commission. Official statistics have made unprecedented achievements on a global scale, which deserves to be celebrated by the statistical community.
In September 2008, the United Nations Statistics Division invited countries, regional institutions and international organizations to express their views on the proposal to celebrate World Statistics Day on October 20, 2010. Although many countries and regions have held statistics day, statistics week or statistics month celebrations in various forms, global statistics day celebrations can better show the great achievements made by official statistics in the world and the important contributions made to economic and social development. This initiative received a wide response during the fortieth session of the United Nations Statistical Commission in February 2009, and 75 countries and international organizations expressed their support. Based on these positive feedbacks, the forty-first session of the United Nations Statistical Commission in February 2010 considered the report on World Statistics Day, and at the 64th session of the United Nations General Assembly, a resolution was made to designate October 20, 2010 as World Statistics Day, inviting governments to support the celebration of World Statistics Day.
Second, the style of previous World Statistics Days
On October 20th, 2010, the United Nations Department of Economic and Social Affairs and the National Bureau of Statistics of China jointly held the first global celebration of "World Statistics Day" in the United Nations Pavilion of the Shanghai World Expo, with the theme of celebrating many achievements of official statistics and promoting the core values of "service, integrity and professionalism" of official statistics, aiming at enhancing public understanding and support for official statistics. Li Keqiang, Deputy Prime Minister of the State Council, China, and Ban Ki-moon, Secretary-General of the United Nations, sent written speeches; The Statistics Department of the United Nations Department of Economic and Social Affairs and the National Bureau of Statistics of China jointly held the launching ceremony of "World Women: 2010" and "Interpretation of Main Statistical Indicators in China", signed the Letter of Intent on International Statistical Training Cooperation between the National Bureau of Statistics of People’s Republic of China (PRC) and the United Nations Statistics Department, and held the opening ceremony of the China International Statistical Training Center-United Nations Statistical Cooperation Center. The celebration of the first World Statistics Day was supported and promoted by about 80 countries around the world, and more than 100 countries around the world held celebrations.
On October 20, 2015, the second World Statistics Day was celebrated in Xi ‘an, China. Nearly 100 statistical officials, experts and scholars from 55 countries and international organizations gathered together to show government statistical achievements, share statistical development experience and advocate statistics to better serve economic and social development and enhance people’s well-being. The theme of this Statistics Day is "Optimizing Data and Improving Life", which has been supported and promoted by national statistical agencies, statistical associations, universities and other partners in more than 110 countries and regions around the world. Promotion activities include holding a press conference, reporting the latest survey or census results, and releasing statistics of interest to the general public, which further expands the influence of official statistics.
The third World Statistics Day was held on October 20th, 2020, with the theme of "Connecting the world with data we can trust", emphasizing the importance of credibility, authoritative data, innovation and public products in the national statistical system. The celebration was organized under the guidance of the United Nations Statistical Commission, and the global statistical agencies made joint efforts to hold various activities to display and publicize statistics. In his invitation letter to all countries, UN Secretary-General Antonio Guterres pointed out: "On the occasion of the 75th anniversary of the founding of the United Nations, the whole world is deploying data to meet common challenges. Let us take the opportunity of World Statistics Day to highlight the important role of statistics in promoting sustainable development."
Logo of previous world statistics days



Third, China Statistics Open Day
The National Bureau of Statistics of China responded positively to the United Nations resolution on celebrating World Statistics Day, and designated September 20th, 2010 as "China Statistics Open Day", and carried out a series of activities with the themes of "Statistics with You" and "Towards Open and Transparent China Statistics". Since then, in mid-September every year, the National Bureau of Statistics will hold a series of activities of the China Statistics Open Day in combination with the major themes and key work of China’s official statistics in that year, and invite grassroots statistical investigators, users of statistical data, teachers and students of colleges and universities, netizens and media reporters and other representatives from all walks of life to the event site for discussion and exchange, so as to enhance the public’s understanding of statistical work and statistical data and promote China statistics to be more open, transparent and better serve the society.
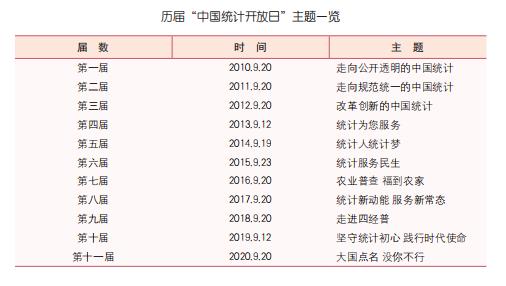
So far, the National Bureau of Statistics has heldThe 11th China Statistics Open Day received great attention from all walks of life, the active participation of the public, and the strong support of statistical institutions at all levels and statisticians. It not only showed the new achievements of China’s statistical reform and development, but also spread statistical knowledge and promoted statistical culture. As a beautiful business card for statistical departments to create sunshine statistics, China Statistics Open Day reflects the attitude of statistical departments to actively adapt to the new situation of China’s economic and social development, open their doors to statistics, and consciously accept social supervision. At the same time, it has become a window to effectively improve statistical ability, statistical data quality and government statistical credibility, and to show the core values of statistics and the mental outlook of statisticians.
(Written by: Ba Yunhong Juan Wang Li Lu Zhao Wei)